1. Prepare Axcient Virtual Office for SonicOS 7.x
| See Configure IPsec VPN site-to-site VPN Settings for details on these preparatory steps. |
NOTE: Release 7.x includes significant user interface differences from SonicOS 6.5 and earlier.
Before you work with the SonicOS 7.x+ firewall, first enable port forwarding and IPsec VPN within your Virtual Office
Note: You may also perform these steps within a Runbook (to simplify testing and live cloud failover events.)
- First, open your Virtual Office.
- Next, enable port forwarding.
- Finally, configure IPsec VPN within your Virtual Office.
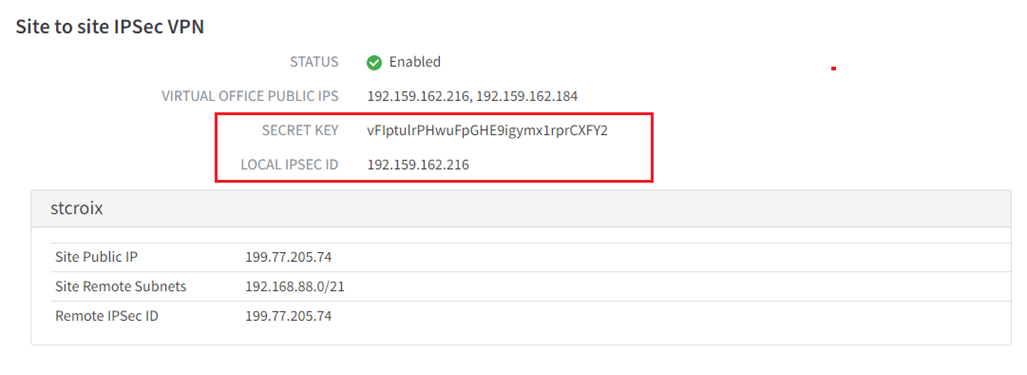
Important: Once you have configured IPsec VPN, please make a note of (a) the randomly generated pre-shared SECRET KEY (password) which was generated for you, as well as (b) the LOCAL IPSEC ID address you configured to use for IPsec VPN.
You will need this information later in this process:
2. Configure your SonicWall firewall for IPsec VPN - SonicOS 7.x
NOTE: This release includes significant user interface differences from SonicOS 6.5 and earlier.
2.0. Create an address object for the local LAN
Navigate to Object | Match Object | Addresses and click Add
- Enter a friendly Name for the address object, i.e. Sonicwall_LAN
- Set Zone Assignment to LAN
- Set Type to Network
- For Network enter the local LAN network address, i.e. 10.198.62.0, etc.
- For Netmask/Prefix length enter the local LAN netmask
Click Save to continue.

3.0. Create an address object for the Virtual Office LAN
3.1. Navigate to Object | Match Object | Addresses and click Add
- Enter a friendly Name for the address object, i.e. Virtual_Office_LAN
- Set Zone Assignment to VPN
- Set Type to Network
- For Network enter the local LAN network address, i.e. 172.16.16.0, etc.
- For Netmask enter the local LAN netmask
Click Save to continue.

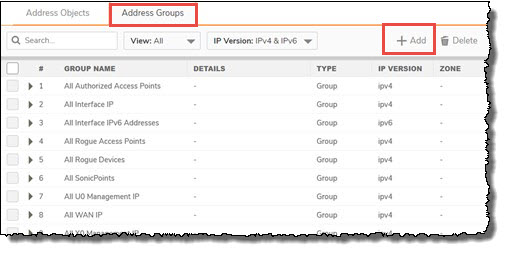
Create an address Group
If your Virtual Office has multiple networks, repeat the steps above to create each network object. Then, create a Group object containing all the Virtual Office LAN networks. Use this Group object when assigning the remote network.
You may also create an address group if you have multiple local LAN networks you wish to connect with Virtual Office over the VPN.
Click Address Groups and click Add to create an address group:
4.0. Enable VPN
4.1. Click Network in the top navigation menu
4.2. Navigate to IPsec VPN | Rules and Settings, and click Settings
4.3. Select Enable VPN
4.4. Navigate to Device | Settings | Administration | Firewall Name and enter a value in Unique Firewall Identifier
Note: As the name implies, this name should be unique and different from any other Sonicwall Firewall under your control.
Click OK to continue.

5.0. Configure VPN policy
5.1. Click Network in the top navigation menu.
5.2. Navigate to IPsec VPN | Rules and Settings and click Add.
The VPN Policy windows is displayed.
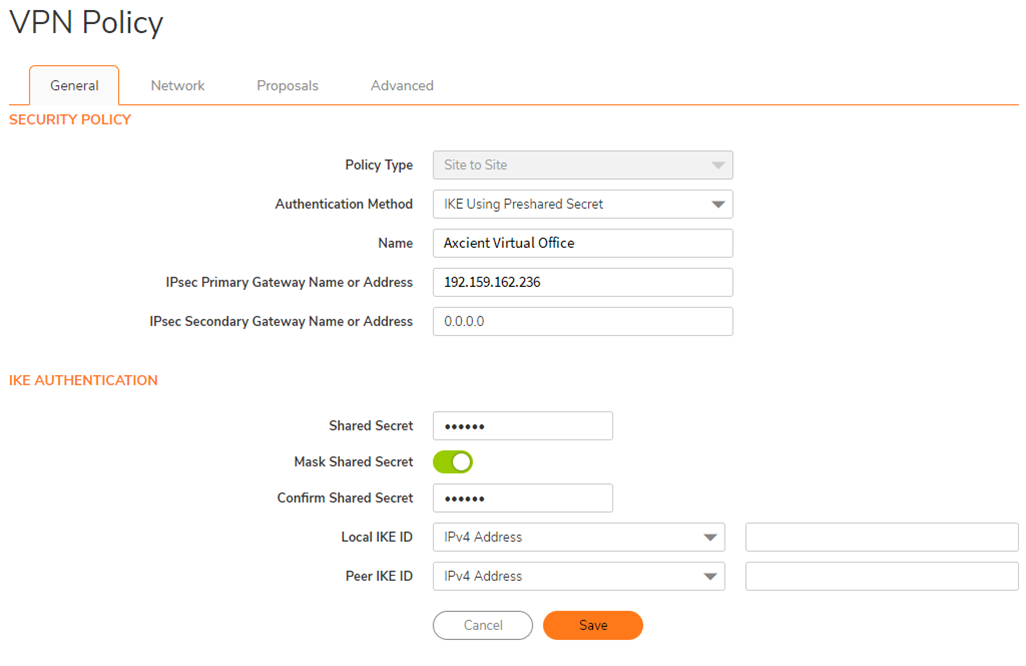
5.3. Select the General menu:
-
Security Policy
- Set Policy Type to Site to Site
- Set Authentication Method to IKE using Preshared Secret
- Enter a friendly Name like ‘Axcient VPN Policy’
- For IPsec Primary Gateway Name or Address, enter the Virtual Office Public IP address. (LOCAL IPSEC ID)
- For IPsec Secondary Gateway Name or Address, enter 0.0.0.0
-
IKE Authentication
- Enter the Secret Key provided in Virtual Office in the Shared Secret and Confirm Shared Secret fields
- Set Local IKE ID and Peer IKE ID to IPv4 Address
Click Save to continue.
5.4. Select the Network menu.
- Under Local Networks, select Choose local network from list and set it to Sonicwall_LAN
- Under Remote Networks, select Choose destination network from list and set it to Virtual_Office_LAN
Click Save to continue.

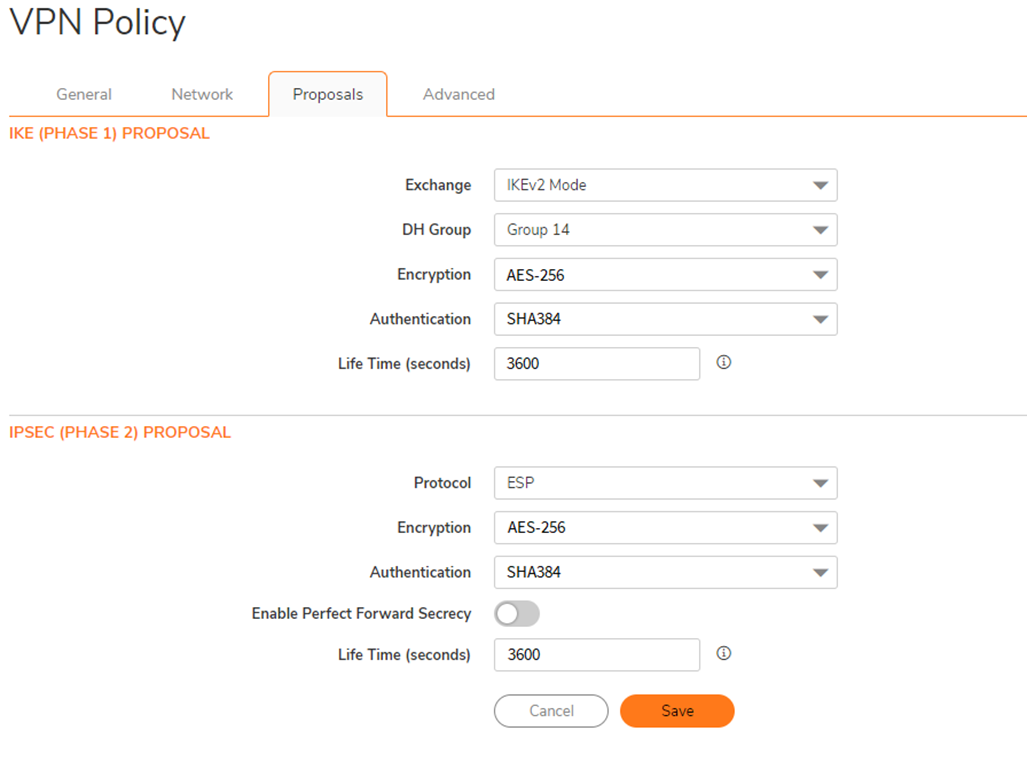
5.5. Select the Proposals menu.
-
IKE (Phase 1) Proposal
- For Exchange select IKEv2 Mode
- For DH Group select Group 14
- For Encryption select AES
- For Authentication select SHA384
-
IKE (Phase 2) Proposal
- For Protocol select ESP
- For Encryption select AES-256
- For Authentication Select either SHA256, SHA384, or SHA512
- Enable Perfect Forward Secrecy is not used, leave disabled
- For Life Time (seconds) enter 3600
Click Save to continue.
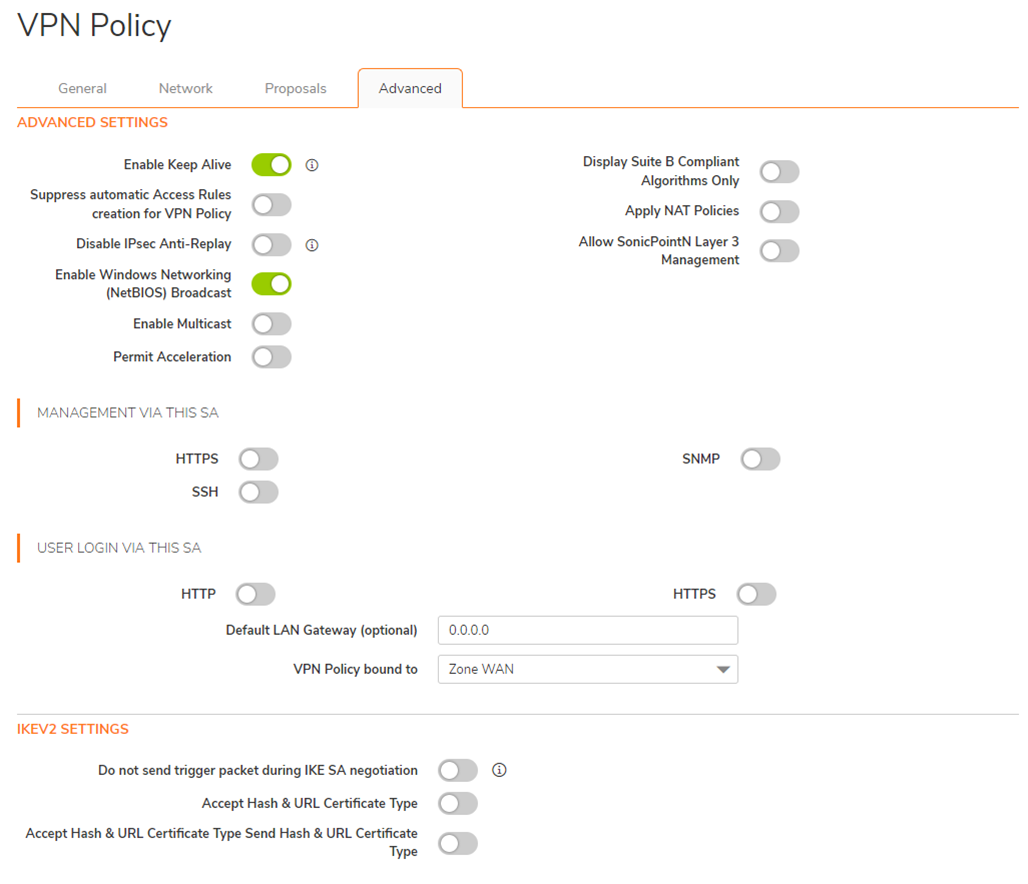
5.6. Select the Advanced menu.
- Select Enable Keep Alive
- Select Enable Windows Networking (NetBIOS) Broadcast
- Set VPN Policy bound to value to Zone WAN
Click OK to save the configuration.
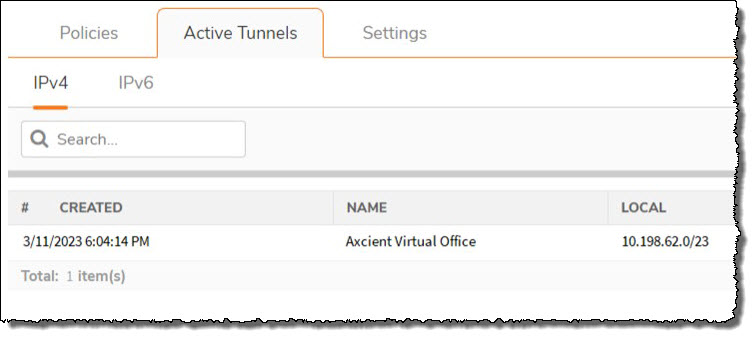
3. Activate the connection
Navigate to IPsec VPN | Rules and Settings and click Active Tunnels.
Verify that tunnel Axcient Virtual Office is present and active.
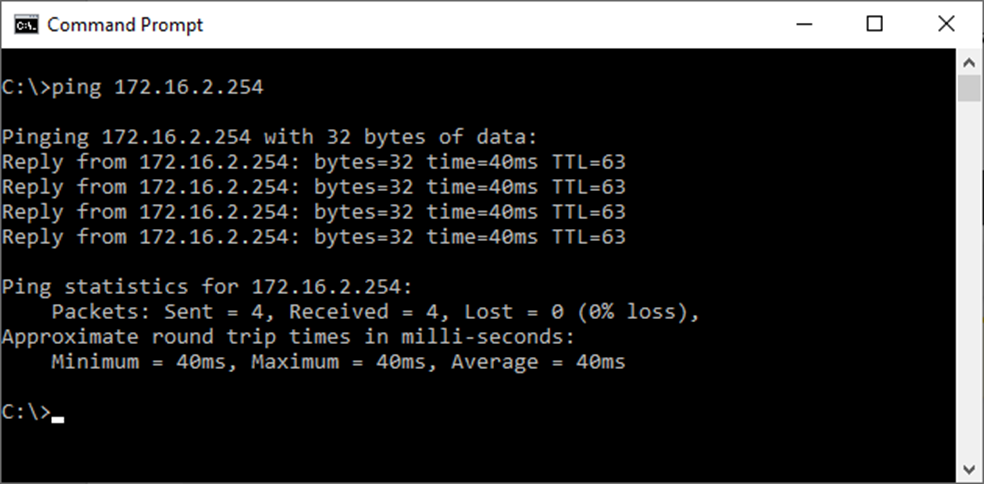
4. Verify your connection
To test your connection, open a Windows CMD shell and ‘ping’ the Virtual Office gateway address.
SUPPORT | 720-204-4500 | 800-352-0248
- Contact Axcient Support at https://partner.axcient.com/login or call 800-352-0248
- Free certification courses are available in the Axcient x360Portal under Training
- Subscribe to the Axcient Status page for status updates and scheduled maintenance
1433